Showing Vaccination Status with Certificate of User on Face Recognition
Objective
The main objective of the project is to show the status of the vaccination using faces rather that the Aadhar.
Abstract
Unauthorized access, which means when someone enters into your device, system or your house without your permission is said to be unauthorized access. Several methods are being used to handle these unauthorized access problems. This project demonstrates to increase the capability of the devices we have constructed. Our proposed method integrates a better approach, intended to advance the cooperativeness of the explore operation. In this work, we develop the application with a device to eradicate the unauthorized access of unknown persons into our premises. Our application can be able to alert the persons whenever any unknown person is trying to enter into our premises.
KEYWORDS: Access, Unauthorized, Application, Deep Learning, Face Detection.
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
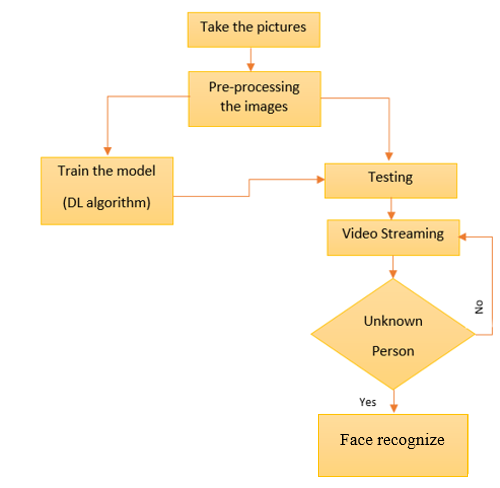
Block Diagram
Specifications
HARDWARE CONFIGURATION:
- Processor: I3/Intel Processor
- Hard Disk:160GB
- RAM: 8Gb
SOFTWARE CONFIGURATION:
- Operating System: Windows 7/8/10
- IDE: Pycharm
- Libraries Used: Numpy, IO, OS, Pillow, Tkinter
- Technology: Python 3.6+
- Accessories : Webcam.
Learning Outcomes
· Scope of Real Time Application Scenarios.
· What is a search engine and how browser can work.
· What type of technology versions are used.
· Use of HTML, and CSS on UI Designs.
· Data Parsing Front-End to Back-End.
· Working Procedure.
· Introduction to basic technologies used for.
· How project works.
· Input and Output modules.
· Practical exposure to
o Hardware and software tools.
o Solution providing for real time problems.
o Working with team/ individual.
o Work on Creative ideas.
· Frame work use.
· About python.





 Paper Publishing
Paper Publishing
