Division and Replication of Data in Cloud for Optimal Performance and Security.
Objective
The main objective of the project is to create division and replication of data to optimize the performance.
Abstract
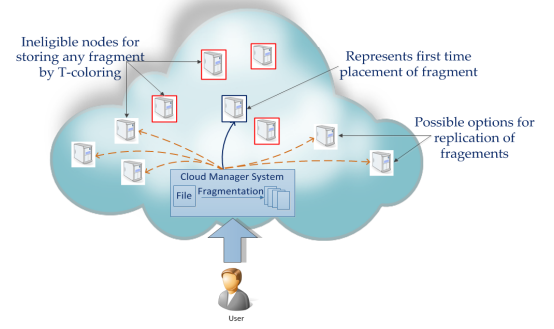
AWS Cloud-based data storage service has drawn increasing interests from both academic and industry in the recent years due to its efficient and low cost management. Since it provides services in an open network, it is urgent for service providers to make use of secure data storage and sharing mechanism to ensure data confidentiality and service user privacy. To protect sensitive data from being compromised, the most widely used method is encryption. merely encrypting data (e.g., via AES) cannot entirely satisfy the actual necessity of data management. Moreover. On the off chance that download demand can be effectively controlled, EDoS attacks can't be launched to prevent customers from receiving a charge out of administration. Outsourcing data to a third-party administrative control, as is done in cloud computing, gives rise to security concerns. The data compromise may occur due to attacks by other users and nodes within the cloud. Therefore, high security measures are required to protect data within the cloud. However, the employed security strategy must also take into account the optimization of the data retrieval time. In this paper, we propose Division and Replication of Data in the Cloud for Optimal Performance and Security (DROPS) that collectively approaches the security and performance issues. In the DROPS methodology, we divide a file into fragments, and replicate the fragmented data over the cloud nodes. Each of the nodes stores only a single fragment of a particular data file that ensures that even in case of a successful attack, no meaningful information is revealed to the attacker. Moreover, the nodes storing the fragments, are separated with certain distance by means of graph T-coloring to prohibit an attacker of guessing the locations of the fragments. Furthermore, the DROPS methodology does not rely on the traditional cryptographic techniques for the data security; thereby relieving the system of computationally expensive methodologies. We show that the probability to locate and compromise all of the nodes storing the fragments of a single file is extremely low. We also compare the performance of the DROPS methodology with ten other schemes. The higher level of security with slight performance overhead was observed.
Keywords – AWS Cloud, Centrality, cloud security, fragmentation, replication, performance
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
Block Diagram
Specifications
Software Requirements
Operating System: Windows 7+
Server side Script: HTML, CSS & JS
IDE: PyCharm
Libraries Used: Pandas, Numpy, OS.
Framework: Flask.
Hardware Requirements
Processor - I3/Intel Processor
RAM- 4GB (min)
Hard Disk- 128 GB
Key Board- Standard Windows Keyboard
Mouse - Two or Three Button Mouse.
Learning Outcomes
· Scope of Real Time Application Scenarios.
· What is a search engine and how browser can work.
· What type of technology versions are used.
· Use of HTML, and CSS on UI Designs.
· Data Parsing Front-End to Back-End.
· Working Procedure.
· Introduction to basic technologies used for.
· How project works.
· Input and Output modules.
· Practical exposure to
o Hardware and software tools.
o Solution providing for real time problems.
o Working with team/ individual.
o Work on Creative ideas.
· Frame work use.
· About python.





 Paper Publishing
Paper Publishing
