Virtex 7 FPGA Implementation of 256 Bit Key AES Algorithm with Key Schedule and Sub Bytes Block Optimization
Also Available Domains Communications and Crypto Core|Xilinx Vivado|Xilinx ISE
Objective
The main objective of this paper is to improve the security by extending the cipher key size into 256 bit key AES algorithm and applied selective transformation for optimization.
Abstract
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
Block Diagram
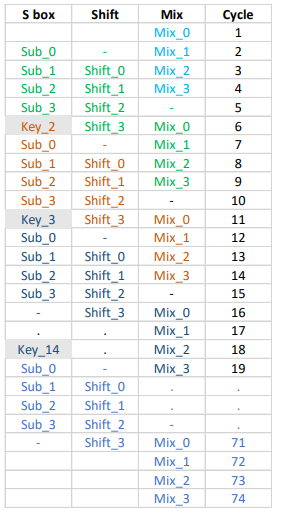
Specifications
Software Requirements:
· Xilinx ISE Tool /Xilinx Vivado
· HDL: Verilog
Hardware Requirements:
· Microsoft® Windows XP,
· Intel® Pentium® 4 processor or Pentium 4 equivalent with SSE support
· 512 MB RAM
· 100 MB of available disk space
Learning Outcomes
- Basics of Digital Electronics
- FPGA design Flow
- Introduction to Verilog Coding
- Different modeling styles in Verilog
o Data Flow modeling
o Structural modeling
o Behavioral modeling
o Mixed level modeling
- Concept of Cryptography systems
- Importance of Crypto systems
- Drawbacks of existing methods
- Introduction to Advanced Encryption standard (AES)
- Knowledge on pipelining concept
- Knowledge on Symmetric, Asymmetric and Hash functions
- Applications of AES in real time
- Scope of AES concept in today’s world
- Applications in real time
· Xilinx ISE 14.7/Xilinx Vivado for design and simulation
· Generation of Netlist
· Solution providing for real time problems
· Project Development Skills:
o Problem Analysis Skills
o Problem Solving Skills
o Logical Skills
o Designing Skills
o Testing Skills
o Debugging Skills
o Presentation Skills
o Thesis Writing Skills





 Paper Publishing
Paper Publishing
