Cyber Threat Predictive Analytics for Improving Cyber Supply Chain Security
Objective
The main objective of this project is to provide recommended relevant controls to tackle cyber threats.
Abstract
Cyber Supply Chain (CSC) system is complex which involves different sub-systems performing various tasks. Security in supply chain is challenging due to the inherent vulnerabilities and threats from any part of the system which can be exploited at any point within the supply chain. This can cause a severe disruption on the overall business continuity. Therefore, it is paramount important to understand and predicate the threats so that organization can undertake necessary control measures for the supply chain security. Cyber Threat Intelligence (CTI) provides an intelligence analysis to discover unknown to known threats using various properties including threat actor skill and motivation, Tactics, Techniques, and Procedure (TT and P), and Indicator of Compromise (IoC). This paper aims to analyse and predicate threats to improve cyber supply chain security. We have applied Cyber Threat Intelligence (CTI) with Machine Learning (ML) techniques to analyse and predict the threats based on the CTI properties. That allows to identify the inherent CSC vulnerabilities so that appropriate control actions can be undertaken for the overall cyber security improvement. To demonstrate the applicability of our approach, CTI data is gathered and a number of ML algorithms, i.e., Logistic Regression (LG), Support Vector Machine (SVM), Random Forest (RF), and Decision Tree (DT), Cat Boost, Gradient Boost are used to develop predictive analytics using the Microsoft Malware Prediction dataset. The experiment considers attack and TTP as input parameters and vulnerabilities and Indicators of compromise (IOC) as output parameters. The results relating to the prediction reveal that Spyware/Ransom ware and spear phishing are the most predictable threats in CSC. We have also recommended relevant controls to tackle these threats. We advocate using CTI data for the ML predicate model for the overall CSC cyber security improvement
Keywords: Logistic Regression (LG), Support Vector Machine (SVM), Random Forest (RF), Decision Tree (DT), Cat Boost, and Gradient Boost.Cyber
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
Block Diagram
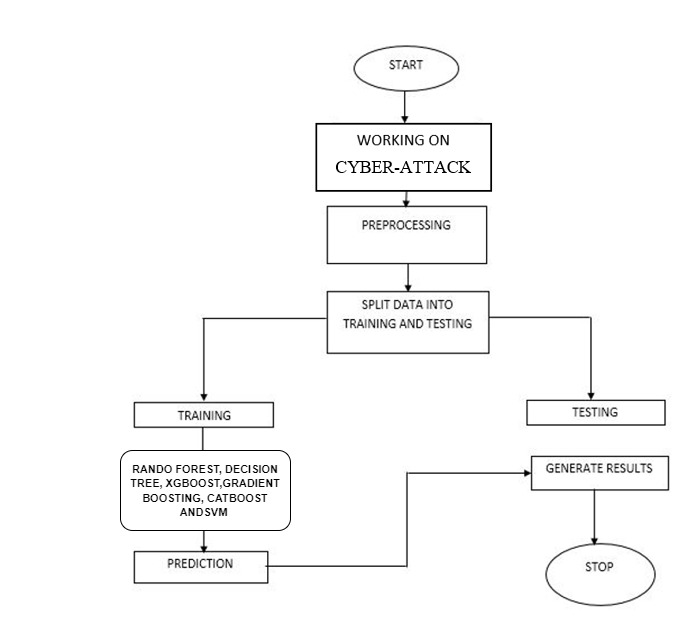
Specifications
Hardware:
- Operating system : Windows 7 or 7+
- RAM: 8 GB
- Hard disc or SSD: More than 500 GB
- Processor : Intel 3rd generation or high or Ryzen with 8 GB Ram
Software:
- Software’s: Python 3.6 or high version
- IDE: PyCharm.
- Framework : Flask
Learning Outcomes
· About Python.
· About PyCharm.
· About Pandas.
· About Numpy.
· About HTML.
· About CSS.
About JavaScript.




 Paper Publishing
Paper Publishing
