Area Reduction AES Algorithm in Hardware Trojan Detection
Objective
The main objective of this project is to implement AES using Trojan Detection approach
Abstract
Hardware Trojan (HT) has lately become a significant problem for computer systems, especially those utilized for mission critical functions like medical or military ones. Effects that have been proposed include everything from the gadget completely malfunctioning to secret information leaking. The Trojans that have been suggested so far have a variety of effects on a device's dependability. There are many types of algorithms but this study considers AES algorithm as AES operates by utilizing a chain of linked operations that replace and shuffle the input data, which is known as the substitution permutation network concept. The sorts of hardware Trojan areas in the AES algorithm are reviewed in this study, along with potential strategies to prevent them. The recommended effort results decrease in the average area.
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
Block Diagram
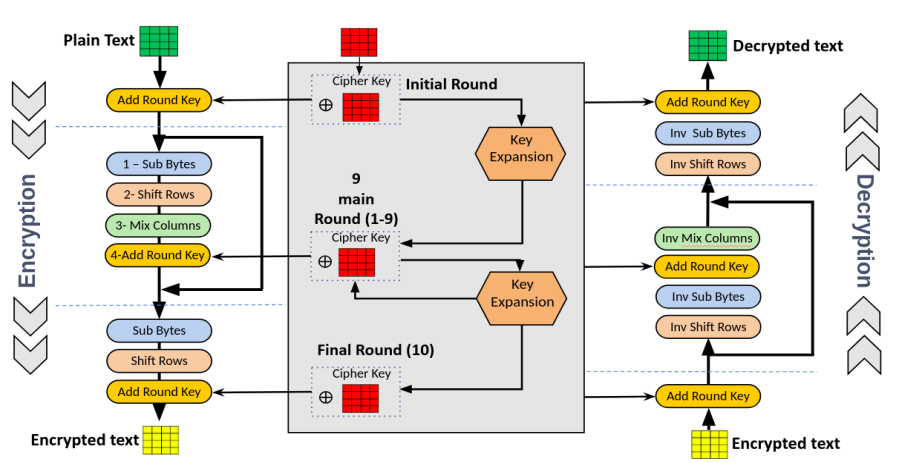
Specifications
Software Requirements:
· Xilinx Vivado2018.3 Tool.
· HDL: Verilog.
Hardware Requirements:
· Microsoft® Windows XP.
· Intel® Pentium® 4 processor or Pentium 4 equivalent with SSE support.
· 512 MB RAM.
· 100 MB of available disk space.
Learning Outcomes
- Basics of Digital Electronics.
- Concept of AES algorithm
- Knowledge on s-box permutations
- Introduction to Verilog Coding.
- Different modeling styles in Verilog.
o Data Flow modeling.
o Structural modeling.
o Behavioral modeling.
o Mixed level modeling.
- About cryptography.
- Knowledge on composite field.
- Applications in real time.
· Xilinx Vivado 2018.3/Xilinx ISE 14.7 Suite for design and simulation.
· Generation of Net list.
· Solution providing for real time problems.
· Project Development Skills:
o Problem Analysis Skills.
o Problem Solving Skills.
o Logical Skills.
o Designing Skills.
o Testing Skills.
o Debugging Skills.
o Presentation Skills.
Thesis Writing Skills




 Paper Publishing
Paper Publishing
