A Secure method for Image Signaturing using SHA 256, RSA, and Advanced Encryption Standard (AES)
Also Available Domains Communications|Xilinx Vivado
Objective
The core idea of this paper is to confirm whether the given image is original or manipulated one. Even though a single pixel varied means it will identify. This will identify using the 3 different algorithms SHA, RSA, AES.
Abstract
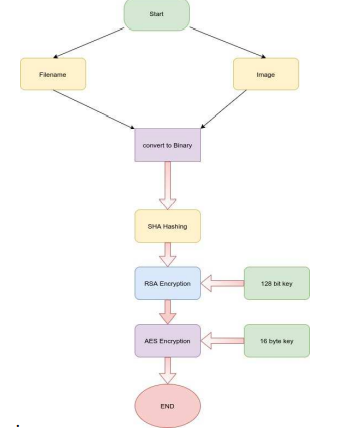
Cryptography is associated with the process of converting ordinary plain text into ambiguous text and vice versa. Hardware Security plays a major role in most of the applications which include net banking, e-commerce, military, satellite, wireless communications, electronic gadgets, digital image processing, etc. There are three types of cryptographic techniques; Symmetric key cryptography, Hash functions and Public key cryptography. Symmetric key algorithms namely Advanced Encryption Standard (AES), and Data Encryption Standard use the same key for encryption and decryption. The signature of the image is done through 3 steps. The three steps include SHA256 (Secure Hash Algorithm 256), RSA (Rivest-Shamir-Adleman), and AES (Advanced Encryption Standard). The signature of the image is stored in a binary file which is sent to the person who needs to verify the image that is already present near the viewer. The method has been tested y artificially applying attacks such as blurring the image greyscale the image and changing one pixel in the image.
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
Block Diagram
Specifications
Software Requirements:
· Xilinx ISE Tool
· Modelsim
· Matlab
· HDL: Verilog
Hardware Requirements:
· Microsoft® Windows XP,
· Intel® Pentium® 4 processor or Pentium 4 equivalent with SSE support
· 512 MB RAM
· 100 MB of available disk space
Learning Outcomes
- Basics of Digital Electronics
- FPGA design Flow
- Introduction to Verilog Coding
- Different modeling styles in Verilog
o Data Flow modeling
o Structural modeling
o Behavioral modeling
o Mixed level modeling
- Concept of Cryptography systems
- Importance of Crypto systems
- Drawbacks of existing methods
- Introduction to Advanced Encryption standard (AES)
- Knowledge on pipelining concept
- Knowledge on Symmetric, Asymmetric and Hash functions
- Applications of AES in real time
- Scope of AES concept in today’s world
- Applications in real time
· Xilinx ISE 14.7/Xilinx Vivado for design and simulation
· Generation of Netlist
· Solution providing for real time problems
· Project Development Skills:
o Problem Analysis Skills
o Problem Solving Skills
o Logical Skills
o Designing Skills
o Testing Skills
o Debugging Skills
o Presentation Skills
Thesis Writing Skills




 Paper Publishing
Paper Publishing
