A Secure Data Dynamics and Public Auditing Scheme for Cloud Storage
Objective
The main aim of the project is to achieve a secure public auditing scheme applying third party auditors to authenticate the privacy, reliability, and integrity of data stored in the cloud. This proposed auditing scheme composes the use of the AES-256 algorithm for encryption, SHA-512 for integrity check and RSA-15360 for public key encryption. And perform data dynamics operation which deals with mostly insertion, deletion, and, modification.
Abstract
Cloud computing is an evolving technology that provides data storage and highly fast computing services at a very low cost. All data stored in the cloud is handled by their cloud service providers or the caretaker of the cloud. The data owner is concerned about the authenticity and reliability of the data stored in the cloud as the data owners. Data can be misappropriated or altered by any unauthorized user or person.
This project desire to suggest a secure public auditing scheme applying third party auditors to authenticate the privacy, reliability, and integrity of data stored in the cloud. This proposed auditing scheme composes the use of the AES-256 algorithm for encryption, SHA-512 for integrity check and RSA-15360 for public key encryption. And perform data dynamics operation which deals with mostly insertion, deletion, and, modification.
Keywords: Cloud Computing, Cloud Storage, Data Integrity, Security, Auditing.
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
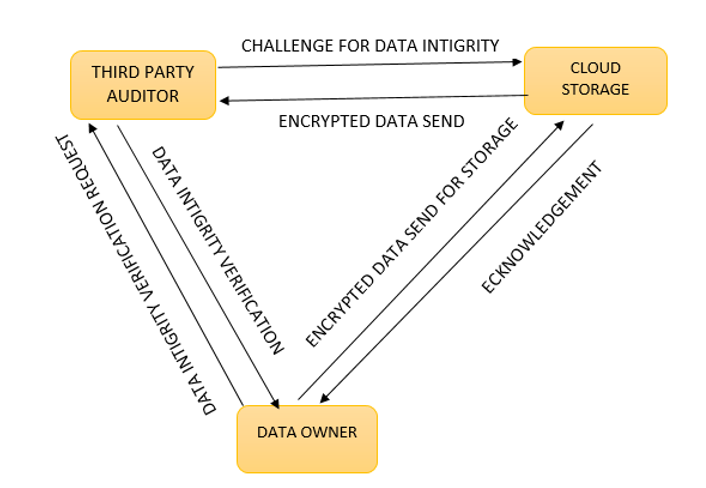
Block Diagram
Specifications
HARDWARE SPECIFICATIONS:
- Processor: I3/Intel
- Processor RAM: 4GB (min)
- Hard Disk: 128 GB
- Key Board: Standard Windows Keyboard
- Mouse: Two or Three Button Mouse
- Monitor: Any
SOFTWARE SPECIFICATIONS:
- Operating System: Windows 7+
- Server-side Script: Python 3.6+
- IDE: PyCharm
- Libraries Used: Pandas,Numpy,os.
Learning Outcomes
- Scope of Real Time Application Scenarios.
- How Internet Works.
- What is a search engine and how browser can work?
- What type of technology versions is used?
- Use of HTML and CSS on UI Designs.
- Data Base Connections.
- Data Parsing Front-End to Back-End.
- Need of Pycharm-IDE to develop a web application.
- Working Procedure.
- Testing Techniques.
- Error Correction mechanisms.
- How to run and Deploy the applications.
- Introduction to basic technologies used for?
- How project works.
- Input and Output modules.
- How to test the project based on user inputs and observe the output.
- MySQL insertion and MySQL database creation.
- Practical exposure to software tools and solution providing for real time problems working with team/ individual work on Creative ideas.
- How cloud computing works?
- Learn about types of algorithms and how to use?
- What is Cloud Storage?
- What is Public Auditing?
- How to Implement Secure Data Dynamics?
- Project Development Skills:
- Problem analysing skills.
- Problem solving skills.
- Creativity and imaginary skills.
- Programming skills.
- Deployment.
- Testing skills.
- Debugging skills.
- Project presentation skills.
- Thesis writing skills.





 Paper Publishing
Paper Publishing
