A Higher-Level Security Scheme for Key Access on Cloud Computing
Objective
The main objective of this project is implementing Shamir’s secret sharing algorithm in cloud computing.
Abstract
In this work, we construct a key access management scheme that seamlessly transitions any hierarchical-like access policy to the digital medium. The proposed scheme allows any public cloud system to be used as a private cloud. We consider the data owner an entity consisting of several organization units. We provide a secure method for each user of this entity to access the public cloud from both inside and outside the company’s network. The idea of our key access control scheme, which is based on Shamir’s secret sharing algorithm and polynomial interpolation method, is suitable especially for hierarchical organizational structures. It offers a secure, flexible, and hierarchical key access mechanism for organizations utilizing mission-critical data. It also minimizes concerns about moving mission-critical data to the public cloud and ensures that only users with sufficient approvals from the same or higher privileged users can access the key by making use of the topological ordering of a directed graph, including self-loop. Main overheads such as public and private storage needs are reduced to a tolerable level, and the key derivation is computationally efficient. From a security perspective, our scheme is both resistant to collaboration attacks and provides key in distinguishability security. Since the key does not need to be held anywhere, the problem of a data breach based on key disclosure risk is also eliminated.
NOTE: Without the concern of our team, please don't submit to the college. This Abstract varies based on student requirements.
Block Diagram
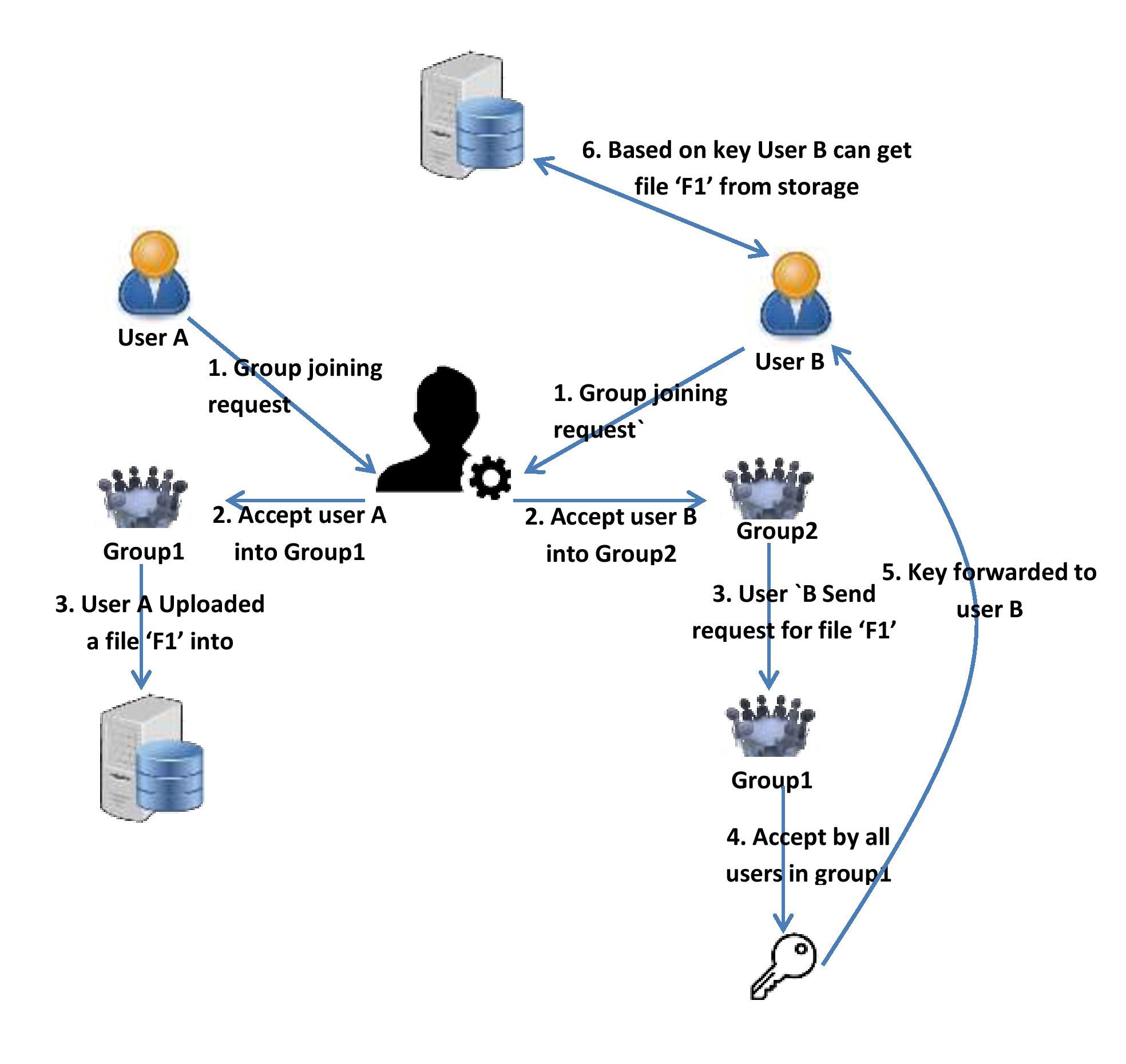
Specifications
H/W System Configurations:
· Processor : I3/Intel Processor (min)
· RAM :8GB (min)
· Hard Disk : 250GB (min).
S/W System Configurations:
· Application Server : Tomcat 9.0
· Front End : HTML, JSP
· Scripts : JavaScript.
· Server side Script : Java Server Pages.
· Database : My SQL 6.0
· Database Connectivity : JDBC
· IDE : Eclipse
Learning Outcomes
· Scope of Real Time Application Scenarios
· How Internet Works
· What is a search engine and how browser can work?
· What is Tomcat server and how they can work?
· What type of technology versions is used?
· Use of HTML and CSS on UI Designs
· Data Base Connections
· Data Parsing Front-End to Back-End
· Need of Eclipse-IDE to develop a web application
· Working Procedure
· Testing Techniques
· Error Correction mechanisms
· How to run and Deploy the applications
· Introduction to basic technologies used for
· How project works
· Input and Output modules
· How to test the project based on user inputs and observe the output
· MySQL insertion and MySQL database creation
· Practical exposure to software tools and solution providing for real time problems working with team/ individual work on Creative ideas.
· How cloud computing works?
· Learn about types of algorithms and how to use?
· What is Public Key encryption?
· Project Development Skills:
o Problem analyzing skills.
o Problem solving skills.
o Creativity and imaginary skills.
o Programming skills.
o Deployment.
o Testing skills.
o Debugging skills.
o Project presentation skills.
o Thesis writing skills.





 Paper Publishing
Paper Publishing
